Abstract: The Internet of Things is a network of people-to-people, people-to-people, things-to-people, and people-to-people interaction. Once its concept was put forward, it has been vigorously promoted and actively developed by governments, scientific research institutions, and various types of companies. The perception layer is the main source of information acquisition for the Internet of Things. Its information security problem is the primary issue facing the development of the Internet of Things. The research on information acquisition methods and existing security threats in the perception layer of the Internet of Things was conducted. The existing security protection mechanisms were analyzed and summarized. Finally, according to the current information security problems of the sensor layer and the development trend of its technology, corresponding countermeasures are proposed.
Keywords: Internet of Things, Perception Layer, Information Security, Recommendations Introduction The Internet of Things is a comprehensive information system with interconnections of perception as the core, and it is the third wave of information industries following computers and the Internet.
Since the concept of Internet of Things emerged, its connotation has been continuously developed and enriched. Although there are many definitions of the Internet of Things in the industry, their meaning is roughly the same. It is generally believed that the Internet of Things should have three basic characteristics: comprehensive perception, reliable transmission, and intelligent processing.
From the perspective of the system structure, the Internet of Things can be divided into three levels: the perception layer, the transmission layer, and the application layer. The sensory layer is at the bottom of the entire system and consists of a large number of devices that have sensing and recognition capabilities. They are used to sense and identify objects and collect environmental information. The transport layer is located in the middle of the entire system, including the converged networks formed by the various communications networks. This part is generally considered to be the most mature part. The application layer is located at the top level of the entire system and combines the Internet of Things technology with industry-specific technologies. Through the storage, mining, processing, and application of information sent at the network layer, the solution integration of a wide range of intelligent applications is realized.
From the perspective of information interaction and interconnection, the future Internet of Things will truly realize the expansion of individuals' interconnections from any time, anywhere and from any time, anywhere, and then expose a large amount of information exposed in public places. Transfer to the network layer and application layer. If such information exposed in public places lacks effective protection measures, it can easily be illegally intercepted, stolen, or interfered. Especially in the advanced stage of the development of the Internet of Things, the entities in the Internet of Things scene all possess a certain ability to perceive, calculate and execute. If these perceptive devices that are widely existed are illegally destroyed or manipulated, they will affect the national foundation, society and individuals. Information security poses new threats. Therefore, the information security of the Internet of Things is an important issue that needs to be solved urgently.
As the basis of the Internet of Things, the perception layer is responsible for sensing and collecting external information and is the source of information for the entire Internet of Things. Therefore, the security protection of the sensory data will be the basis of the information security of the entire Internet of Things. This article will focus on the analysis of the information security of the Internet of Things sensory layer, and gives corresponding countermeasures.
1. Information Sensing Layer Information Security Analysis of the Internet of Things The sensing layer is composed of a variety of devices that have the ability to sense, identify, control, and execute. It collects data on items and surrounding environments and completes the recognition and recognition of the physical world. The two key technologies for the perception layer to perceive physical world information are Radio Frequency Identification (RFID) technology and Wireless Sensor Network (WSN) technology. Therefore, the security of data information in the perception layer of the Internet of Things is discussed. The focus is on the security of RFID systems and WSN systems.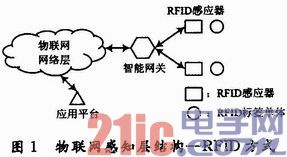
RFID technology is a non-contact automatic identification technology realized through radio frequency communication. The sensing layer structure of the Internet of Things based on RFID technology is shown in Figure 1. Each RFID system is accessed as an independent network node to the network layer through a gateway. Therefore, the information security under this system architecture relies on the information security of a single RFID system.
The security risks that RFID systems face are mainly the following:
(1) Information leakage: The information is read without the knowledge of the end device or RFID tag user (information privacy is compromised).
(2) Tracking: Using the fixed information on the RFID tag, the carrier of the RFID tag is tracked (location privacy is compromised).
(3) Replay attack: The attacker eavesdrops on the response information of the electronic tag and retransmits this information to a legitimate reader/writer to achieve an attack on the system.
(4) Clone attack: Clone end-devices, imposter replacement, and attack the system.
(5) Information modification: The eavesdropping information is modified and then transmitted to the original recipient.
(6) Man-in-the-Middle Attack: The attacker disguises itself as a legitimate reader to obtain the response information of the electronic tag, and uses this information to disguise itself as a legitimate electronic tag to respond to the reader. In this way, the attacker can obtain legal reader authentication before the next round of communications.
In response to the above security risks, the industry has put forward various solutions, which are analyzed as follows:
(1) Failing the label: killing the label and sleeping the label When the merchandise is delivered, the RFID label on the merchandise is killed or put into a sleep state, so that the RFID label cannot work, and the leakage of user privacy is effectively prevented. Killing tags makes the tags unusable and wasteful. Although sleeping labels can be recycled, the operation is complicated and safety is limited.
(2) Active shielding and active interference Using aluminum foil shopping bags (Faraday shielding) or using electronic devices to actively transmit interference signals to prevent RFID tags from being identified. The former method increases costs and cannot be implemented on a large scale. The latter method will cause interference to other communication systems.
(3) The use of cryptographic knowledge to introduce security mechanisms Based on the knowledge of cryptography, using cryptographic algorithms and security authentication mechanisms to implement information security in RFID systems is a hot topic in the industry, and a large number of low-cost security authentication protocols have been proposed, such as hash- Lock protocol, randomized Hash-lock protocol, Hash-chain protocol, Hash-based IDvariation protocol, interactive authentication protocol, David's digital book management RFID protocol, distributed RFID query-response authentication protocol, LCAP protocol, and re-encryption mechanism. For RFID systems, security and cost are two major factors that need to be weighed against each other. Therefore, it is difficult to find a security authentication mechanism that is suitable for all RFID applications.
At the same time, the diversity of RFID standards and the lack of relevant security assessment standards also pose great challenges for the design and evaluation of RFID security mechanisms. Therefore, it is recommended that the security requirements of the actual application of the Internet of Things be divided, and the corresponding RFID system security levels should be divided, and corresponding security mechanisms should be designed for the specific security requirements of each security level.
The wireless sensor network is an important sensing data source for the sensing layer, and its information security is also an important part of the information security at the sensing layer. Based on the sensor technology, the sensing layer structure of the Internet of Things is shown in Fig. 2. The sensor nodes form a sensor network in the form of an autonomous network through short-range wireless communication technology, and access to the network layer via a gateway node to form information transmission and sharing.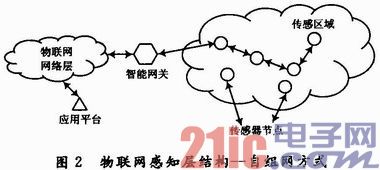
Compared with the traditional network, the wireless sensor network has the characteristics of limited node resources (processing power, storage capacity, limited communication capacity, and low power consumption), large deployment volume (low cost), and complex network topology. The main security risks it faces are the following:
(1) Physical capture of nodes: Attackers use external means to illegally capture sensor nodes (gateway nodes and ordinary nodes). Physical trapping of nodes is divided into two cases. One is capture by ordinary nodes, which can control the receipt and transmission of node information, but it does not acquire the authentication and transmission keys of nodes, and cannot tamper with and falsify effective node information to perform system attacks; One is full control, that is, the node's authentication and transmission keys are obtained, and the entire system can be attacked. In this case, if the captured node is a gateway node, the security of the entire network will be lost.
(2) Sensing Information Leakage: An attacker can easily monitor the information transmitted in a single or multiple communication links to obtain sensitive information.
(3) Exhaustion attack: Exhaust node energy through continuous communication.
(4) Congestion attack: After the attacker obtains the center frequency of the target network communication frequency, the radio wave is transmitted near this frequency point to perform interference, and all sensor nodes in the attack node communication radius cannot work normally.
(5) Unfair attacks: Attackers constantly send high-priority packets to occupy the channel, causing other nodes to be at a disadvantage in the communication process.
(6) Denial-of-service attacks: The ability to degrade the availability of the network and reduce a certain desired function of the network or system.
(7) Forwarding attacks: similar to replay attacks in RFID systems.
(8) Node replication attack: An attacker places a copy of a controlled node in multiple locations in the network and causes network inconsistency.
For the above attack methods, the industry has proposed many protection measures, such as strengthening the security protection of gateway node deployment environment, strengthening the security control of sensor network confidentiality, and adding node authentication mechanisms and intrusion detection mechanisms. Similarly, the deployment of security protection measures in wireless sensor networks is also constrained by the capabilities of nodes. Many mature security mechanisms in traditional networks cannot be directly applied.
2. Information Security Recommendations for the Internet of Things at the Perception Layer In combination with the characteristics and development trends of the Internet of Things awareness technology, the following aspects should be considered in the construction of information security at the perception level of the Internet of Things:
(1) From the perspective of information security (integrity, confidentiality, authenticity, availability, etc.), according to the specific application requirements, the security level of the perception layer subsystem is divided, and the security elements that are required for each security level are defined. Its scope of application.
The proposed radio frequency identification system security classification is shown in Table 1.
(2) Strengthen the study of key management systems Because of the limitations of their computational resources, the sensing layer network nodes mostly choose key management protocols based on symmetric key systems. There are mainly three types of key management protocols: based on key distribution center methods, pre-distribution methods, and Clustering method. Key management systems based on symmetric key systems often target only certain special application scenarios and cannot completely resist hardware attacks or internal attackers (where nodes are trapped). Although the key management protocol based on the asymmetric key system is more secure, the computational complexity is greatly increased, and it is still not widely used in wireless sensor networks.
Therefore, a key management system oriented to the perception layer of the Internet of Things must provide a lightweight symmetric and asymmetric cryptosystem. The design and implementation of lightweight cryptographic algorithms is an important part of key management system research.
(3) Establishing a sound route mechanism for security The secure routing mechanism ensures that the network can still perform correct route discovery, construction, and maintenance when it is threatened and attacked. At present, the wireless sensor network routing protocols proposed by scholars at home and abroad are mostly aimed at completing the data transmission between nodes with minimum communication, calculation, and storage overhead, and are vulnerable to various types of attacks. Therefore, the security routing algorithm designed for various security threats is a key research direction.
(4) Strengthen the authentication and access control mechanism of the node The authentication and access control mechanism can prevent unauthorized users from accessing the nodes and data of the perception layer of the Internet of Things, effectively ensuring the security of the data of the sensing layer. At present, the main authentication technologies in the sensor network include authentication technologies based on lightweight public key algorithms, authentication technologies based on pre-shared keys, authentication technologies based on random key pre-distribution, and authentication technologies based on single hash functions. There are many similarities between light-weight security authentication protocols that are researched in the field of RFID and they can be used for reference and integration. At the same time, when deploying the nodes, full consideration should be given to the specific application requirements and the actual capabilities of the nodes, and appropriate levels of authentication and access control mechanisms should be implanted.
(5) Establishing an effective tolerant and fault-tolerant mechanism. Perceived networks lack physical security in traditional networks. Nodes are vulnerable to attacks (capture, destruction, or compromise). Therefore, establishing an effective tolerant and fault-tolerant mechanism is crucial for ensuring the normal operation of the sensing network. When designing fault tolerance and fault tolerance mechanisms, various application environments and attack methods should be fully considered, and the balance between false positive rate and missed detection rate should be handled properly.
3. Conclusion The perception layer serves as the basis of the Internet of Things. Its information security is a prerequisite for the sustainable and effective development of the Internet of Things in China. This paper analyzes and combs the status quo of data security in the perception layer of the Internet of Things, and proposes some recommended measures to protect the information security of the Internet of Things at the sensing layer. China is at the initial stage of the construction of the Internet of Things. The simultaneous establishment and improvement of the IoT security protection mechanism is of great significance. Dividing system security levels according to actual application requirements and deploying corresponding security protection mechanisms for security levels should be a correct construction idea.
Keywords: Internet of Things, Perception Layer, Information Security, Recommendations Introduction The Internet of Things is a comprehensive information system with interconnections of perception as the core, and it is the third wave of information industries following computers and the Internet.
Since the concept of Internet of Things emerged, its connotation has been continuously developed and enriched. Although there are many definitions of the Internet of Things in the industry, their meaning is roughly the same. It is generally believed that the Internet of Things should have three basic characteristics: comprehensive perception, reliable transmission, and intelligent processing.
From the perspective of the system structure, the Internet of Things can be divided into three levels: the perception layer, the transmission layer, and the application layer. The sensory layer is at the bottom of the entire system and consists of a large number of devices that have sensing and recognition capabilities. They are used to sense and identify objects and collect environmental information. The transport layer is located in the middle of the entire system, including the converged networks formed by the various communications networks. This part is generally considered to be the most mature part. The application layer is located at the top level of the entire system and combines the Internet of Things technology with industry-specific technologies. Through the storage, mining, processing, and application of information sent at the network layer, the solution integration of a wide range of intelligent applications is realized.
From the perspective of information interaction and interconnection, the future Internet of Things will truly realize the expansion of individuals' interconnections from any time, anywhere and from any time, anywhere, and then expose a large amount of information exposed in public places. Transfer to the network layer and application layer. If such information exposed in public places lacks effective protection measures, it can easily be illegally intercepted, stolen, or interfered. Especially in the advanced stage of the development of the Internet of Things, the entities in the Internet of Things scene all possess a certain ability to perceive, calculate and execute. If these perceptive devices that are widely existed are illegally destroyed or manipulated, they will affect the national foundation, society and individuals. Information security poses new threats. Therefore, the information security of the Internet of Things is an important issue that needs to be solved urgently.
As the basis of the Internet of Things, the perception layer is responsible for sensing and collecting external information and is the source of information for the entire Internet of Things. Therefore, the security protection of the sensory data will be the basis of the information security of the entire Internet of Things. This article will focus on the analysis of the information security of the Internet of Things sensory layer, and gives corresponding countermeasures.
1. Information Sensing Layer Information Security Analysis of the Internet of Things The sensing layer is composed of a variety of devices that have the ability to sense, identify, control, and execute. It collects data on items and surrounding environments and completes the recognition and recognition of the physical world. The two key technologies for the perception layer to perceive physical world information are Radio Frequency Identification (RFID) technology and Wireless Sensor Network (WSN) technology. Therefore, the security of data information in the perception layer of the Internet of Things is discussed. The focus is on the security of RFID systems and WSN systems.

RFID technology is a non-contact automatic identification technology realized through radio frequency communication. The sensing layer structure of the Internet of Things based on RFID technology is shown in Figure 1. Each RFID system is accessed as an independent network node to the network layer through a gateway. Therefore, the information security under this system architecture relies on the information security of a single RFID system.
The security risks that RFID systems face are mainly the following:
(1) Information leakage: The information is read without the knowledge of the end device or RFID tag user (information privacy is compromised).
(2) Tracking: Using the fixed information on the RFID tag, the carrier of the RFID tag is tracked (location privacy is compromised).
(3) Replay attack: The attacker eavesdrops on the response information of the electronic tag and retransmits this information to a legitimate reader/writer to achieve an attack on the system.
(4) Clone attack: Clone end-devices, imposter replacement, and attack the system.
(5) Information modification: The eavesdropping information is modified and then transmitted to the original recipient.
(6) Man-in-the-Middle Attack: The attacker disguises itself as a legitimate reader to obtain the response information of the electronic tag, and uses this information to disguise itself as a legitimate electronic tag to respond to the reader. In this way, the attacker can obtain legal reader authentication before the next round of communications.
In response to the above security risks, the industry has put forward various solutions, which are analyzed as follows:
(1) Failing the label: killing the label and sleeping the label When the merchandise is delivered, the RFID label on the merchandise is killed or put into a sleep state, so that the RFID label cannot work, and the leakage of user privacy is effectively prevented. Killing tags makes the tags unusable and wasteful. Although sleeping labels can be recycled, the operation is complicated and safety is limited.
(2) Active shielding and active interference Using aluminum foil shopping bags (Faraday shielding) or using electronic devices to actively transmit interference signals to prevent RFID tags from being identified. The former method increases costs and cannot be implemented on a large scale. The latter method will cause interference to other communication systems.
(3) The use of cryptographic knowledge to introduce security mechanisms Based on the knowledge of cryptography, using cryptographic algorithms and security authentication mechanisms to implement information security in RFID systems is a hot topic in the industry, and a large number of low-cost security authentication protocols have been proposed, such as hash- Lock protocol, randomized Hash-lock protocol, Hash-chain protocol, Hash-based IDvariation protocol, interactive authentication protocol, David's digital book management RFID protocol, distributed RFID query-response authentication protocol, LCAP protocol, and re-encryption mechanism. For RFID systems, security and cost are two major factors that need to be weighed against each other. Therefore, it is difficult to find a security authentication mechanism that is suitable for all RFID applications.
At the same time, the diversity of RFID standards and the lack of relevant security assessment standards also pose great challenges for the design and evaluation of RFID security mechanisms. Therefore, it is recommended that the security requirements of the actual application of the Internet of Things be divided, and the corresponding RFID system security levels should be divided, and corresponding security mechanisms should be designed for the specific security requirements of each security level.
The wireless sensor network is an important sensing data source for the sensing layer, and its information security is also an important part of the information security at the sensing layer. Based on the sensor technology, the sensing layer structure of the Internet of Things is shown in Fig. 2. The sensor nodes form a sensor network in the form of an autonomous network through short-range wireless communication technology, and access to the network layer via a gateway node to form information transmission and sharing.

Compared with the traditional network, the wireless sensor network has the characteristics of limited node resources (processing power, storage capacity, limited communication capacity, and low power consumption), large deployment volume (low cost), and complex network topology. The main security risks it faces are the following:
(1) Physical capture of nodes: Attackers use external means to illegally capture sensor nodes (gateway nodes and ordinary nodes). Physical trapping of nodes is divided into two cases. One is capture by ordinary nodes, which can control the receipt and transmission of node information, but it does not acquire the authentication and transmission keys of nodes, and cannot tamper with and falsify effective node information to perform system attacks; One is full control, that is, the node's authentication and transmission keys are obtained, and the entire system can be attacked. In this case, if the captured node is a gateway node, the security of the entire network will be lost.
(2) Sensing Information Leakage: An attacker can easily monitor the information transmitted in a single or multiple communication links to obtain sensitive information.
(3) Exhaustion attack: Exhaust node energy through continuous communication.
(4) Congestion attack: After the attacker obtains the center frequency of the target network communication frequency, the radio wave is transmitted near this frequency point to perform interference, and all sensor nodes in the attack node communication radius cannot work normally.
(5) Unfair attacks: Attackers constantly send high-priority packets to occupy the channel, causing other nodes to be at a disadvantage in the communication process.
(6) Denial-of-service attacks: The ability to degrade the availability of the network and reduce a certain desired function of the network or system.
(7) Forwarding attacks: similar to replay attacks in RFID systems.
(8) Node replication attack: An attacker places a copy of a controlled node in multiple locations in the network and causes network inconsistency.
For the above attack methods, the industry has proposed many protection measures, such as strengthening the security protection of gateway node deployment environment, strengthening the security control of sensor network confidentiality, and adding node authentication mechanisms and intrusion detection mechanisms. Similarly, the deployment of security protection measures in wireless sensor networks is also constrained by the capabilities of nodes. Many mature security mechanisms in traditional networks cannot be directly applied.
2. Information Security Recommendations for the Internet of Things at the Perception Layer In combination with the characteristics and development trends of the Internet of Things awareness technology, the following aspects should be considered in the construction of information security at the perception level of the Internet of Things:
(1) From the perspective of information security (integrity, confidentiality, authenticity, availability, etc.), according to the specific application requirements, the security level of the perception layer subsystem is divided, and the security elements that are required for each security level are defined. Its scope of application.
The proposed radio frequency identification system security classification is shown in Table 1.

(2) Strengthen the study of key management systems Because of the limitations of their computational resources, the sensing layer network nodes mostly choose key management protocols based on symmetric key systems. There are mainly three types of key management protocols: based on key distribution center methods, pre-distribution methods, and Clustering method. Key management systems based on symmetric key systems often target only certain special application scenarios and cannot completely resist hardware attacks or internal attackers (where nodes are trapped). Although the key management protocol based on the asymmetric key system is more secure, the computational complexity is greatly increased, and it is still not widely used in wireless sensor networks.
Therefore, a key management system oriented to the perception layer of the Internet of Things must provide a lightweight symmetric and asymmetric cryptosystem. The design and implementation of lightweight cryptographic algorithms is an important part of key management system research.
(3) Establishing a sound route mechanism for security The secure routing mechanism ensures that the network can still perform correct route discovery, construction, and maintenance when it is threatened and attacked. At present, the wireless sensor network routing protocols proposed by scholars at home and abroad are mostly aimed at completing the data transmission between nodes with minimum communication, calculation, and storage overhead, and are vulnerable to various types of attacks. Therefore, the security routing algorithm designed for various security threats is a key research direction.
(4) Strengthen the authentication and access control mechanism of the node The authentication and access control mechanism can prevent unauthorized users from accessing the nodes and data of the perception layer of the Internet of Things, effectively ensuring the security of the data of the sensing layer. At present, the main authentication technologies in the sensor network include authentication technologies based on lightweight public key algorithms, authentication technologies based on pre-shared keys, authentication technologies based on random key pre-distribution, and authentication technologies based on single hash functions. There are many similarities between light-weight security authentication protocols that are researched in the field of RFID and they can be used for reference and integration. At the same time, when deploying the nodes, full consideration should be given to the specific application requirements and the actual capabilities of the nodes, and appropriate levels of authentication and access control mechanisms should be implanted.
(5) Establishing an effective tolerant and fault-tolerant mechanism. Perceived networks lack physical security in traditional networks. Nodes are vulnerable to attacks (capture, destruction, or compromise). Therefore, establishing an effective tolerant and fault-tolerant mechanism is crucial for ensuring the normal operation of the sensing network. When designing fault tolerance and fault tolerance mechanisms, various application environments and attack methods should be fully considered, and the balance between false positive rate and missed detection rate should be handled properly.
3. Conclusion The perception layer serves as the basis of the Internet of Things. Its information security is a prerequisite for the sustainable and effective development of the Internet of Things in China. This paper analyzes and combs the status quo of data security in the perception layer of the Internet of Things, and proposes some recommended measures to protect the information security of the Internet of Things at the sensing layer. China is at the initial stage of the construction of the Internet of Things. The simultaneous establishment and improvement of the IoT security protection mechanism is of great significance. Dividing system security levels according to actual application requirements and deploying corresponding security protection mechanisms for security levels should be a correct construction idea.
Medical Terminals And Connectors
Medical Terminals,Medical Connectors,Medical Tubing Connectors,Stainless Steel Fitting
Yihua Precision Machining Co, Ltd. , https://www.yhmachining.com